- home
- articles
- quick answersQ&A
-
discussionsforums
- CodeProject.AI Server
- All Message Boards...
- Application Lifecycle>
- Design and Architecture
- Artificial Intelligence
- ASP.NET
- JavaScript
- Internet of Things
- C / C++ / MFC>
- C#
- Free Tools
- Objective-C and Swift
- Database
- Hardware & Devices>
- Hosting and Servers
- Java
- Linux Programming
- Python
- .NET (Core and Framework)
- Android
- iOS
- Mobile
- WPF
- Visual Basic
- Web Development
- Site Bugs / Suggestions
- Spam and Abuse Watch
- featuresfeatures
- communitylounge
- help?
Everything / Security / Cryptography
Cryptography
cryptography
Great Reads
by Arpan Jati
RSA encryption library with full OAEP padding and private key encryption support
by Kewin Rausch
Design and development of a TOR-like protocol to keep your communication secure and your identity unknown
by Cryptonite
The Blum Micali algorithm provides for a cryptographically secure PRNG (pseudo random number generator).
Latest Articles
by Daniel Ramnath
C++,
by Daniel Ramnath
C++ OpenSSL 3.
by Michael Chourdakis
Use SHA-3 and the CRYSTALS Kyber,
by Sergey Alexandrovich Kryukov
Generator of highly secure passwords based on cryptographic hash and master password,
All Articles
2 Sep 2012 by
can we break the encryption, all i found by google and experiments is:The first line of a file (78MB 8n size) (database of a free religious books software) contains these strings "Standard ACE DB" "M i c r o s o f t b a s e c r y p t o g r a g h i c p r o v i d e r" (reading in c#,...
20 Mar 2019 by Ger Hayden
The RSACryptoServiceProvider is not implemented in .NET Core yet so while I have managed to generate keys I cannot get Encrypt or Decrpyt to work so I need my own alternatives. I cant find anything useful on line to guide me. The logic I want to implement is 1. Client calls API for RSA public...
20 Mar 2019 by MadMyche
Which part of RSA is missing? MS Docs NetCore 2.1 | RSACryptoServiceProvider Class[^]
11 Apr 2016 by Toni Andika
RSA algorithm:1. Select two different prime numbers p and q. For security aim, the integer's p and q must be large.2. Calculate n = p * qn will be used as the module for public key and private key and n is also known as key_component.3. Calculate f(n) = (q-1)(p-1), where f is a function...
11 Apr 2016 by Kornfeld Eliyahu Peter
RSA[^] is RSA, not matter what bit size you choose...But it is better to use larger, probably the largest available (4096 today with public libraries), and in any case not less than 2048 (1024 bit was proved as breakable in 2003)...
16 Jul 2017 by RealFlare
How do you crypt a file with RSA-2048 using a button. I know that it will crypt the file using a public key, and decrypt the file using a private key. What I have tried: I have tried to find the source code on google, but it never works.
16 Jul 2017 by CPallini
16 Feb 2022 by charles henington
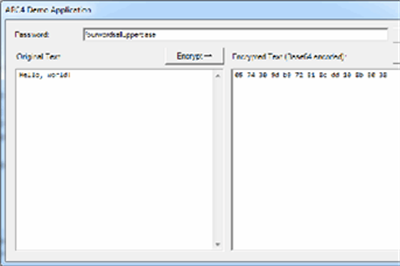
Simple user defined Cipher Transform that I got the idea from https://www.codeproject.com/Articles/5319044/ARC4-Encryption-Library
25 Aug 2012 by Joezer BH
Hey all, I need a good hash function (for strings) that will produce the same hash value for a specific string on different platforms, My app invovles a server farm, and a "bank" server, Each server produces hash "keys" for strings and the bank stores the keys.The Servers may later...
26 Aug 2012 by Kenneth Haugland
How about the build in class in .NET:http://msdn.microsoft.com/en-us/library/system.security.cryptography.rsacryptoserviceprovider.aspx[^]
27 Mar 2012 by Marian Placko
This article shows a simple hack of a built-in MS SQL Server WITH ENCRYPTION mechanism
1 Feb 2013 by Member 9804140
Hello. I have such function. But there is an error: "R6010 - abort has been called". Could anyone help me with this error?void Encrypt (char *pszFile, char *pszSecret) { int size; char *buf; _bstr_t cipherText; string name; ifstream in (pszFile, ios::in | ios::binary |...
1 Feb 2013 by Matthew Faithfull
That's an unusual error. R6010 is an abort from the C library, MSVCRT in this case. I'd check that your program really gets as far as the line you've indicated. (by setting a breakpoint) If so then you must be doing some serious memory corruption. If not than my guess would be you've got the...
29 Dec 2010 by jk chan
10 Feb 2022 by Michaelred54
I get this error: "An object reference is required for the non-static field, method, or property 'HashAlgorithm.ComputeHash(byte[])'" on this code: protected void Button1_Click(object sender, EventArgs e) { ...
10 Feb 2022 by Tony Hill
Try this HashAlgorithm myHashAlgorithm = HashAlgorithm.Create("SHA512"); byte[] hash = myHashAlgorithm.ComputeHash(Encoding.UTF8.GetBytes(PIN_Entry.Text)); string MyHash = System.BitConverter.ToString(hash); ...
10 Feb 2022 by M Imran Ansari
In order to use a non-static field, method, or property, you must first create an object of an instance. HashAlgorithm hashAlgo = HashAlgorithm.Create("SHA512"); Now use the object hashAlgo to call their methods. Reference for more information:...
20 Apr 2011 by thecobaia
Is there any way to add content "file" to the signed message? In Msdn docs has: http://msdn.microsoft.com/en-us/library/aa382052(v=vs.85).aspxAdding content to the encoded message. But I wanted to add to the message and not make a message only with the data.I have a signed message .p7s...
3 Feb 2013 by manuthebos
10 Dec 2018 by OriginalGriff
Quote: i have done encrypted mention code in c-Arduino and want to decrypted it into c# but when we try to decrypt it in c# receiving different error We can't help you directly - there are too many variables, and we can't run both sides of your code under the same circumstances. So the first...
10 Dec 2018 by alisolution
Greeting, I want to codes which create Encryption in Arduino-C and can be Decrypted into c#. is it possible ? Using algorithm AES or any other an algorthim anyone help me, can provide codes AJ What I have tried: #include "AES.h" #include "base64.h" AES aes; void setup() { ...
19 Aug 2023 by adriancs
I have just published an article exactly answered this question. I know my post it's a little late to the party, but anyway, here's my article. cheers AES Encrypted Data Transmission between Arduino (ESP32) and C# (ASP.NET)[^]
8 Dec 2010 by The.Z
Hi.I have to encrypt a string with AES - PKCS7 Padding in VB.NET.I don't know anything about en/decryption and I have asked google before...but without a result.. :( I have received this description to do that:The PKCS #7 padding string consists of a sequence of bytes, each of...
15 Dec 2010 by The.Z
Hmm..This topic is still active..I need help with this problem..Can somebody help me, please?Best Regards,Z
6 Oct 2014 by Pavel Durov
This article will explain briefly how to use a basic encryption/decryption on Android and on .NET platforms, with focus on passing encrypted data from Android to .NET.
16 Apr 2015 by Hidhoud1991
I'm receiving this error on apple push notificationSystem.Security.Cryptography.CryptographicException: The system cannot find the file specified. at System.Security.Cryptography.CryptographicException.ThrowCryptographicException(Int32 hr) at...
5 Jun 2013 by compuknow
There are are many kinds of ciphers like caesar cipher,Vigenère Cipher,Bifid Cipher and many mor but how can these cipher techniques be applied to a binary file like a .exe file ?
5 Jun 2012 by Eng_Anas
Hi everybody I'm a last year computer science student and I have to design a graduation projectI asked my professors and advice me to design a c sharp program using based on cryptography like a program to implement a DES and RSA application and to do some comparison between the both...
5 Jun 2012 by Maciej Los
I'm not sure what you want to achieve, what kind of comparision do you want to do, but i recommend you to read this: http://wiki.answers.com/Q/What_are_the_difference_between_DES_and_RSA_algorithm[^] - as shortest answer as it's possible ;)More...
15 Sep 2012 by BrianHamilton
Is there any need to use IDisposable in the block of code below. I am availing of using and hash contains the SHA1 of text taken in from the user and inputData is a byte array. I assume the second block of code is correct.Example 1:using (SHA1 hash = SHA1.Create()){ txtSHA1.Text =...
15 Sep 2012 by Kuthuparakkal
Go with second option, if you are able to use "using" statement means, that object is inherited from IDisposable class, they have written appropriate dispose events.
8 Feb 2022 by Pavel Bashkardin
28 Jan 2016 by Reddy1111
when the below function is used to generate RSA key pair of 1024 bits.rsa_key = RSA_generate_key ( 1024, 3, NULL, NULL );keyPair = BIO_new ( BIO_s_mem ( ) );PEM_write_bio_RSAPrivateKey(keyPair, rsa_key, NULL, NULL, 0, NULL, NULL);keyPair_len = BIO_pending(keyPair);Then...
5 Mar 2021 by Clark Fieseln
Low rate data exchange (e.g., chat) using audio steganography, ensuring privacy, anonymity and cybersecurity
30 Mar 2015 by Florian Rappl, Niki Kilbertus
Using Microsoft Azure to add advanced machine learning capabilities with connected IoT devices, which monitor activities of a baby and his or her environment.
27 Mar 2020 by Asish6542165
I have a function that returns a bitcoin address but I want to perform base58check encoding on it to convert it to a bitcoin address. unsigned char address[]="008f26a17cbbc941a9dbe63a1f1c69591f08aab94bd586ad5e" The address is stored in an...
27 Mar 2020 by Richard MacCutchan
OK, this is what it is: Base58Check encoding - Bitcoin Wiki[^]
14 Nov 2019 by CPallini
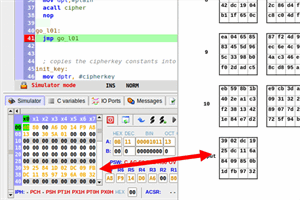
An assembly implementation of the AES-128 cipher algorithm for the 8051 microcontroller
16 Oct 2013 by Member 10339581
Which language offers a better scope for AES encryption/decryption. C++,Python,C# or Java.
20 Nov 2011 by Dominik Reichl
A C# implementation of the BLAKE hash algorithm.
16 Jun 2014 by OriginalGriff
We do not condone, support or assist in the production of malicious code in any way, form or manner. This is a professional site for professional developers. If you want to know how to create such things, you need to visit a hacking site: but be sure to disable all firewalls and antivirus...
8 Sep 2014 by amsainju
19 Mar 2020 by OriginalGriff
Repost: Deleted. Please do not post the same question multiple times: it duplicates work and that annoys people. Annoying people is not the best way to get them to help you ...
17 May 2014 by akhil lal
Hi,I need to create an application in c# which will communicate with SafeNet's HSM Device. As of now i am assiged with a task that this C# console application could interact with the HSM device and check a particular key is valid or not.For this , I have installed ptkc-sdk...
19 Jul 2015 by FelisPhasma
Hello fellow coders,I have recently been doing some work with cryptography in C#. I compiled my program to test the algorithm and I got an error message from JIT saying: "Padding is invalid and cannot be removed" I have looked at many other questions on the internet about this, and most of...
19 Jul 2015 by OriginalGriff
The problem is almost certainly the final part of your method: return new ASCIIEncoding().GetString(ret);Converting a byte array to a string using any form of encoding is likely to give you a string that can't be converted back to the original array of bytes.Try it: instead of returning a...
17 Apr 2011 by Dave Kreskowiak
You're going to have to do what anyone else is going to do. Google for "Cryptography serpent tiger whirlpool".
28 Oct 2016 by Deepraj Thuraka
Tweaking of the Bouncy Castle library to make it work with SecP128r1 curve1251
20 Oct 2021 by sreeyush sudhakaran
I have tried many Examples in Google to PGP Encrypt my Text file , but all of them shows error in some or other ways.I tried the Encryption Tool https://www.igolder.com/PGP/[^] for testing my file.It only works fine in that website only.I hardly need help for 1)How to generate...
20 Oct 2021 by sinchan rane
2 Jan 2012 by Wendelius
Few possible implementations:- https://code.google.com/p/csharptest-net/source/browse/src/Library/Crypto/WhirlpoolManaged.cs[^]- http://code.google.com/p/winhasher/[^]
13 Jul 2011 by Prashant 1986
Hi,If we signed a XML file using C# XML (System.Security.Cryptography.Xml); Will the digital signature same when we create a digital signature using VC++ CryptoAPI for XML file.ThanksPrashant Joseph.
19 Jul 2011 by Sergey Alexandrovich Kryukov
No. It's never the same, practically, otherwise the signature would not protect anything. :-)[EDIT]From OP reply I feel this is not clear. See my comment below. It needs understanding of some...
27 Feb 2011 by reena d.k
I need a progam in C++ that implements the blowfish algorithm and can be used to encrypt and decrypt a text file.Thanks in advance!
27 Feb 2011 by Manfred Rudolf Bihy
There is an article here on CP: A C++ Implementation of the Blowfish Encryption/Decryption method[^].Hope that helps you!
16 Apr 2011 by LaxmikantYadav
Hi Reena,Please find out the source code of Blowfish algorithm on below link.Down load from http://www.schneier.com
14 Aug 2023 by Daniel Ramnath
C++ OpenSSL 3.1 Attack AES-CBC using Padding Oracle Attack, and Timing Attack
19 Sep 2020 by Dave Kent 305
I was making some research on cryptography for a class when i got to this article talking about how the meet in the middle algorithm process can boost the processing time (computational time) of some math problems in python I.E Large Numbers. But...
19 Sep 2020 by Patrice T
Quote: Can i please have a proper explanation of the 'Meet in the middle' mathematical algorithm? In the article you provided, "meet in the middle trick" is itself a link to an explanation (thus the green color) with example. Meet in the middle...
11 Feb 2013 by POP_POP_R3T
I have been playing around with the Microsoft Crypto API. Using CALG_RC4 I am trying to encrypt a plaintext where the key is derived from an md5 hash of the plaintext.I have verified that the "password" md5, ciphertext and lengths of both buffers are the same when I pass them to the decrypt...
11 Feb 2013 by POP_POP_R3T
Ok I figured it out.Turns out I had my blinders on...in two partsFirst:even though my first comment to Andrew's point mentions setting "final" on my call to encrypt I still managed to overlook the flag (arg3) and never finalize encryption. Whoops!Second: When calling...
25 Feb 2011 by Mario Majčica
6 Mar 2014 by Dan Mihajlov
13 Aug 2023 by Michael Chourdakis
16 Mar 2011 by rohitketkar
Hi everyone,I want to compare ECC and RSA. I have read papers regarding that ECC is faster than RSA and has better security per key bit size. Can anyone tell me how i can show this using specific code.
16 Mar 2011 by Sergey Alexandrovich Kryukov
It's nearly impossible to compare security. Comparing security means breaking the cipher of real-life size of the key. Do you have any idea how much resources it may take? :-)Come to think about, the possibility of easy experimental comparison would present a back door (please see the...
30 Jun 2022 by raddevus
Fully working sample code and explanation of everything necessary to create authenticated encryption with AES256.
7 Feb 2019 by Sibeesh Passion
Create own cryptocurrency and own private consortium network in Azure
22 Feb 2020 by Morbiddeath
Hi, I have copied this piece of code from another site and have trouble compiling it; I'm new to cryptography and whilst I tried my best to get this to work, i keep getting "Expression: _BLOCK_TYPE_IS_VALID(pHead->nBlockUse)" I know this error has to do with the heap but I didn't perform any...
21 Aug 2013 by Morbiddeath
I found the solution myself; while compiling the source code of CryptoPP, in the solution properties(cryptdll), under C/C++ menu there is a sub-menu called Code Generation, the field Runtime Library should be Multi-threaded Debug DLL (/MDd). Thanks for your time guys. Farewell.
5 May 2022 by Jerome Vonk
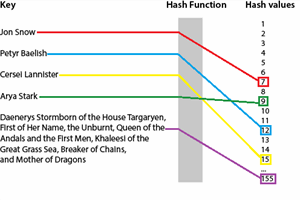
Description of cryptographic hashes and practical examples on how to calculate them
11 Oct 2013 by ASP.NET Community
At A large part of security in any web application is keeping your secrets secret. Cryptography makes that
23 Apr 2012 by Mabchour 1989
Dear all,I'm working on a project that i'm almost done with it but I have a little problem. I'm almost done with my C# code and till the end my client asked me to encrypt data before storing it in the database. I obviously can't redo all the project it'll be time consuming so what I thought...
23 Apr 2012 by Reza Ahmadi
Hi,Have you tried these posts:http://www.4guysfromrolla.com/articles/022107-1.aspx[^]http://msdn.microsoft.com/en-us/library/cc837966%28v=sql.100%29.aspx[^]the second one is applied to 2005 and 2008I hope it helps,Cheers
22 Jul 2013 by Behno0o0oD
Hi every oneI am working on a project which is running on an embedded pc and I am developing by C# language in visual studio 2008 and I have a database using sql server ce.I want my code and my exe file not to be decompiled.what is the best solution?TnX
22 Jul 2013 by OriginalGriff
Pretty much the only thing you can do is look at Obfuscating your exe file - Google can help: Google[^]
22 Jul 2013 by Thomas Daniels
Hi,It's not possible to prevent decompling for a .NET application.But you can try to obfuscate your application. This doesn't prevent decompiling, but it makes the decompiled code very hard to understand for a human. However, there're de-obfuscators, but obfuscating can probably help...
15 Jun 2011 by amruthch
Hi All,Is there any cryptography system developed in which the key is not sent from server to client for decryption.I mean the keys are extracted via some other methods at the client side itself to decrypt! anybody knows?Please help me.
15 Jun 2011 by Sergey Alexandrovich Kryukov
How can you ask questions in such form: "anybody knows"? Many people here know this very well.First, if keys exist, they always send somewhere. Now, I feel you did not get it. How do you think, is it possible that two parties never meet, exchange data using some open channel and still can...
15 Jun 2011 by sam_ckp
15 Jun 2011 by TorstenH.
simple approach:Decrypt in JAVA problem[^]..for "not so much security" systems. Depends on what you want to transmit on the network. this is a useful way when the stuff "just should not be readable by everybody". Implement that on both sides in case.
16 Jun 2011 by Nagy Vilmos
If you use any half-decent comms solution you don't need to worry about how it is done. Let the comms layer deal with this for you. Look at VPN[^] and SHTTP[^] for two good examples.
29 Apr 2015 by Muhamad Faizan Khan
why the decryption result is not right? var encrypted = CryptoJS.AES.encrypt("faizan", "sp"); alert(encrypted); var decrypted = CryptoJS.AES.decrypt(encrypted, "sp"); alert(decrypted);using https://code.google.com/p/crypto-js/[^]
29 Apr 2015 by Peter_in_2780
If you read the documentation at the link you gave, you will see that the return from decrypt is NOT a string.Try usingalert(decrypted.toString(CryptoJS.enc.Utf8));just as the example does.
7 Jan 2023 by Nikhil Sisodia
Hi,I am seeing a strange behavior with CryptStringToBinary Cryptography API.Please see the below code (config: x64 Debug):#include "stdafx.h"#include #include #include #include void main(){ DWORD dwSkip; DWORD dwFlags; DWORD...
6 Oct 2013 by Garth J Lancaster
you're telling the API you're passing the input in as base-64 >> CRYPT_STRING_BASE64yet "MyTest" isnt a base-64 coded 'string'I wouldnt blame the api for chucking a mental, personally - its behaviour seems normal to me
4 May 2013 by Sumon562
I have generated a crystal report. I used ADO.Net connection to generate the report. Then I have brought some change in the query. The problem is when I updated from database expert then I could not find any new field that I have added in the query.Please give me a solution.
5 May 2013 by _Damian S_
Open your crystal report in design view. Locate the data source and click "Verify Database". Log on with the appropriate user and password, and the missing fields will magically appear!
7 Aug 2012 by Member 9324904
I am implementing custom membership user. In which i want to do add my column to store additional information of a user into the membership table. I want to add my own columns into the membership columnsAny one plz help Thanks
7 Aug 2012 by Christian Amado
You can Add your column in database (e.g. aspnet_users table), modify stored procedures that affects to your modified table. That's all from DB.Now in your aspnet project, Add a new class that extends from Membership or MembershipUser depends on your requirements. Add the property (column of...
26 Jul 2022 by raddevus
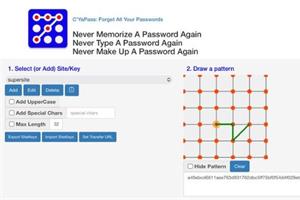
C’YaPass (Fully Open Source Software) now a Fully-Functioning Password Ecosystem which doesn’t store your passwords anywhere — You are the owner of your data.
18 May 2018 by Thaana Paana
I'm trying to decrypt a string that contains a image in a page source, I see that image's path in Inspect Element but I can't get it from there so I'm trying to decrypt using CryptoJS.net version. Here is what I found the most least that is close to simple. This ones from stackoverflow and seems...
13 Jun 2013 by compuknow
I wrote a code to generate a public key and a private key value. Below is the code :void keys(long long int &e_key,long long int &d_key,long long int phival) { e_key = genrndnum(100,(phival-1)); while(gcd(e_key,phival)!=1) { e_key =...
24 Feb 2015 by arunkx
I have an encrypted string (encoded with a key using HMACSHA256). Now how can I decrypt it back using the key and HMACSHA256 algorithm?