- home
- articles
- quick answersQ&A
-
discussionsforums
- CodeProject.AI Server
- All Message Boards...
- Application Lifecycle>
- Design and Architecture
- Artificial Intelligence
- ASP.NET
- JavaScript
- Internet of Things
- C / C++ / MFC>
- C#
- Free Tools
- Objective-C and Swift
- Database
- Hardware & Devices>
- Hosting and Servers
- Java
- Linux Programming
- Python
- .NET (Core and Framework)
- Android
- iOS
- Mobile
- WPF
- Visual Basic
- Web Development
- Site Bugs / Suggestions
- Spam and Abuse Watch
- featuresfeatures
- communitylounge
- help?
Everything / Security / Cryptography
Cryptography
cryptography
Great Reads
by Arpan Jati
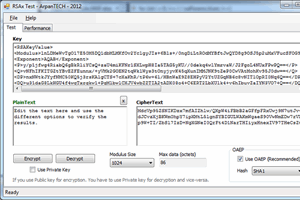
RSA encryption library with full OAEP padding and private key encryption support
by Kewin Rausch
Design and development of a TOR-like protocol to keep your communication secure and your identity unknown
by Cryptonite
The Blum Micali algorithm provides for a cryptographically secure PRNG (pseudo random number generator).
Latest Articles
by Daniel Ramnath
C++,
by Daniel Ramnath
C++ OpenSSL 3.
by Michael Chourdakis
Use SHA-3 and the CRYSTALS Kyber,
by Sergey Alexandrovich Kryukov
Generator of highly secure passwords based on cryptographic hash and master password,
All Articles
1 Feb 2011 by
I didn't read it, but this might answer your question:http://www.webdav.org/specs/draft-leach-uuids-guids-01.txt[^]
18 Apr 2011 by #realJSOP
Like Nish said, there are way too many factors, situations, and possible requirements. We have no idea of the environment you're in, how secure it has to be, or anything even remotely associated with access control. It's a decision only you can make.
30 Jun 2011 by #realJSOP
25 Feb 2021 by #realJSOP
There are several OpenSSL-specific NuGet packages available. I don't know if any of them will meet your needs, but you can start looking in there.
26 Jan 2015 by 1337Architect
Handy classes to use the .NET Encryption/Decryption
5 May 2013 by _Damian S_
Open your crystal report in design view. Locate the data source and click "Verify Database". Log on with the appropriate user and password, and the missing fields will magically appear!
29 Aug 2013 by AaZocco
i am trying to develop a cross platform application that will run on windows, iphone and android. and i would like to implement AES256 encryption for every platform. so my question is:does AES256 encryption for each system will be compatible among them? i mean if i encrypt using AES256...
27 Apr 2015 by Abhinav S
30 May 2011 by abhinav11
Q. Is there any open source library which can be used on Linux for Licensing & Product Activation related stuff? If No, then is there any near by alternative?Detailed Q. : The Licensing scheme is as follows:1. A unique Serial No./Product Key is assigned to user2. A public key (pgp) or a...
25 Oct 2021 by ADMGNS
19 Aug 2023 by adriancs
I have just published an article exactly answered this question. I know my post it's a little late to the party, but anyway, here's my article. cheers AES Encrypted Data Transmission between Arduino (ESP32) and C# (ASP.NET)[^]
15 May 2013 by Adrijan Seferi
25 Apr 2012 by Aescleal
If you're not familiar with classes and header files you're going to have fun implementing anything in C++. If I were you I'd wrap my head around includes and abstract data types and then use libcrypto which is part of the OpenSSL[^] distribution. It's a C library rather than a C++ one but it's...
24 Aug 2011 by affan546
Hi,I am doing VB programming. I just have started. I want to know how the programmers make codes like strings and loops and their by passing ways and their methodology of making new programs ......applications. I want to learn the source codes creation methods. Help me out...
8 Dec 2015 by Afzaal Ahmad Zeeshan
Actually, you have not shown the implementation of this class. The following two snippets are just the "pseudo-code" for the algorithm. What do you think, did you implement it? Does the code work well? From the code, it is clear that i is zero, so only the first block would execute and a few...
17 May 2014 by akhil lal
Hi,I need to create an application in c# which will communicate with SafeNet's HSM Device. As of now i am assiged with a task that this C# console application could interact with the HSM device and check a particular key is valid or not.For this , I have installed ptkc-sdk...
21 May 2014 by akhil lal
27 minutes ago|LINKHI all,How to retrieve the public key, which is exported and saved in a disk using c#. And then i need to convert it to RSAPublickey type.Or i have a public key in my disk .So now i want to read that file and create an RSAPublickey object from that.How that can be...
2 Oct 2010 by Alain Rist
Applied Crypto++: Block Ciphers[^] Sample 1 does not use std::string, so you can adapt the sample code to your needs.cheers,AR
8 Jun 2011 by Alan N
I think the issue is nothing to do with encryption but is related to the decode/encode cycle shown on the right hand side of the diagram.array(A) - Decode -> String (B) - Encode -> array(C)Your code does not show the full details of this conversion but implies that you are...
1 Dec 2015 by Albert Holguin
Here[^] are the build instructions for Windows (32bit, there's a different doc for 64bit). After you've built and installed the openssl libraries, add the include paths (openssl/include or inc32/) to your Visual Studio library paths and the library binary paths (openssl/lib or out32dll/) to your...
11 Mar 2011 by Albin Abel
First you have to decide which hash algorithm has to use. Because once you hashed the files then changing the algorithm will be a waste. There are lot of hash algorithms with .Net framework, Keyed and Non-Keyed. Each has different purpose. For example MD5 is good at small files. But for very...
18 Oct 2018 by Alek Massey
You could change your program to also allow inputs of an encrypted string and of the private key and then use the key to decrypt the string.
4 Jul 2011 by Alexander Galkin
Besides the cryptographic information about your actual key, the key files always contain some metadata, as to when the key was generated, whether it is packed, if so what kind of packing (base64 etc) was used to pack the key etc.Try to open your key in a notepad to see if you can get any...
20 Aug 2013 by Alexander Van Berg
30 Nov 2012 by Alexandre Bencz
Hi :)I'm studying some things about cryptography, and I wonder what is the best system of 128-bit encryption, and how to implement in C/C++ or C#.ThanksAlexandre
31 Dec 2019 by ali_heidari_
hi...i am using rijndeal to encrypt and decrypt some data! but it gives me this error :Padding is invalid and cannot be removed.i searched much but nothing help me to solve this error! tis is my encrypt/decrypt codes:public string Encrypt(string text) { mainRM = new...
10 Dec 2018 by alisolution
Greeting, I want to codes which create Encryption in Arduino-C and can be Decrypted into c#. is it possible ? Using algorithm AES or any other an algorthim anyone help me, can provide codes AJ What I have tried: #include "AES.h" #include "base64.h" AES aes; void setup() { ...
21 Apr 2011 by All Time Programming
Verifying the Server Certificate on the client side using a CA file
25 Apr 2011 by All Time Programming
1 Mar 2011 by amruthch
HiI wanna know the programming assumption made for the POINT AT INFINITY(O)in elliptic curve cryptography,which is the basis for finding the order of generating point or the base point in (Fp)i.e nG=O how can i calculate n?and an assumption for O?thanks[edit]Subject: don't SHOUT! All...
15 Jun 2011 by amruthch
Hi All,Is there any cryptography system developed in which the key is not sent from server to client for decryption.I mean the keys are extracted via some other methods at the client side itself to decrypt! anybody knows?Please help me.
8 Sep 2014 by amsainju
17 Jun 2020 by AnasMHDAbbas
Hi friends, we know RSA key pair need p,q (prime numbers), and if we want to generate RSA key on 128 bit length we need to generate p and q on 128 bit length and do some math with them. my problem is how to generate these big prime numbers and...
13 Apr 2024 by Andre Oosthuizen
You are generating the nonce incorrectly. Your 'sodium.randombytes_buf(i)' function expects the argument of 'i' to be the length of the buffer (in bytes) to be generated, not the actual value of the nonce length as per your code. The...
16 Apr 2013 by AnotherKen
I have not been able to find a clear example of how to store an encryption key in a key container using C#. I can generate my own keys and use them to encrypt and decrypt data. Now I am wondering two things:1. Is it realistic to consider the Microsoft key containers as a reasonably secure...
23 Oct 2014 by AnotherKen
Thanks Bhanu Raja. That is almost identical to what I have implemented now, but I appreciate your attempt to answer the question.
18 Apr 2011 by apaka
I have a small app that needs user credentials to operate. Whats the best way(library) to store those credentials for later use using .NET Thanks in advance.
13 May 2020 by Apprieu (Apprieu)
15 Oct 2013 by Aravind.V.S
23 Dec 2012 by Areff
Hi every body, I am new to RSA and Cryptography and i need to encrypt and decrypt data using RSA,I have a java program which generates a key pair and save them in a .key files with XML format, then I want to use them in .net application , I am importing the keys to be used for encrypt and...
7 Aug 2012 by ariez88
Hello,I have published version 1.3 of an smart client application on my intranet. The deployment goes fine. However, when I try to install the application on my system from intranet I encounter following problems.A. "The publisher can not be verified. Are you sure you want to install...
15 Jul 2012 by Arpan Jati
RSA encryption library with full OAEP padding and private key encryption support
24 Feb 2015 by arunkx
I have an encrypted string (encoded with a key using HMACSHA256). Now how can I decrypt it back using the key and HMACSHA256 algorithm?
19 Feb 2022 by Asif Bahrainwala
19 Mar 2020 by Asish6542165
I want some help with the implementation of sha256 and ripemd160 hash in the c program. Does anyone know how can I perform sha256 on a char array? I wrote a code #include #include #include int main...
19 Mar 2020 by Asish6542165
I want to code a c program to perform ripemd160 hash on a char array. But I cannot figure out how could I do it. Can anyone suggest a c code to do the following? What I have tried: I came across this function in OpenSSL but I cannot figureout...
20 Mar 2020 by Asish6542165
I wrote a c program to calculate ripemd160 hash on a 64-byte char array.But it give me the wrong output. This is my code: #include #include #include int main (void) { unsigned char s[7] =...
20 Mar 2020 by Asish6542165
I wrote a c program to perform sha256 hash on a char array and then perform ripemd160 hash on the output of the sha256 hash function. here is my code: #include #include #include #include
22 Mar 2020 by Asish6542165
just follow this link. SHA256 and RIPEMD160HASH in C program[^] when I replace const unsigned char* rawdata =...
27 Mar 2020 by Asish6542165
I have a function that returns a bitcoin address but I want to perform base58check encoding on it to convert it to a bitcoin address. unsigned char address[]="008f26a17cbbc941a9dbe63a1f1c69591f08aab94bd586ad5e" The address is stored in an...
11 Oct 2013 by ASP.NET Community
At A large part of security in any web application is keeping your secrets secret. Cryptography makes that
9 Apr 2014 by atul sharma 5126
hello all,I am new to cryptography and need you urgent help.* I want to generate a set of asymmetric keys based on a password.* Use Private key to encrypt a string to cipher text* Use public key in my program to decrypt the cipher text from a text file* Use the decryped information...
21 Aug 2018 by Avinash6474
Hi All,How to encrypt image with AES algorithm? How much is the size difference (increase/decrease)after encryption? Is it possible to perform encryption with java script ? Thank you for your suggestions in advance...:)--Avinash
18 Mar 2015 by BacchusBeale
To split a line you need:string[] data = csv.Split(new char[]{','});or make char array e.g: delimiter="," string[] data = csv.Split(delimiter.ToCharArray());Also 11th column is 10, 12th column is 11.
4 Jul 2011 by Balaji_Reddy
hi their , I have generated private and public key in java. whereas public key size is 1kb and private key size is 2kb. i googled lot but unable to understand the core. help me out.Thanks in advance:)
29 Aug 2011 by barneyman
I'm in the process of creating a bunch of attribute certificates, using custom X509 extensions, that all works; this is just the backgroundWhen those certificates are displayed in the MMC Certificate Snapin, the OID's of my attributes aren't registered, so under the Certificate Details tab,...
5 Dec 2012 by BC @ CV
22 Jul 2013 by Behno0o0oD
Hi every oneI am working on a project which is running on an embedded pc and I am developing by C# language in visual studio 2008 and I have a database using sql server ce.I want my code and my exe file not to be decompiled.what is the best solution?TnX
7 Mar 2012 by Bernhard Hiller
There are several things to look at:- are the data on the original stick really PCM data, or are the encrypted? I.e. can you play these data with e.g. Windows Media Player, Audacity, etc.?- the communication between the USB stick and the keyboard. It looks like the keyboard reads some more...
13 Aug 2014 by Bhanu Pratap Verma
Dear All,I have created Key container with the help of "RSACryptoServiceProvider", Now I want to encrypt and decrypt with the help of key which store in key container.Please help me out Its very urgent.Your replied will be highly appreciated.CspParameters cp = new...
18 Aug 2014 by Bhanu Pratap Verma
Hi All,My client required to encrypt password using symmetric key cryptography(Private Key).When user account will be created then password of the user will be encrypted and save in the database table with the help of the private key.The private key should be change with some...
18 Aug 2014 by Bhanu Pratap Verma
24 Sep 2014 by Bhanu Pratap Verma
I have some client requirement to save the key in key container, I have already generated key and I want to store it in the key container. Is it possible to do it?I am using AES algorithm to encrypt and decrypt data.Please follow the below code.public string Encrypt_AES(string...
24 Sep 2014 by Bhanu Pratap Verma
Dear All,I have created key which can we change once in a month, Now I want to store own 64 bit key in microsoft key container. So please help me out for the same.If we use CspParameters class it automatic generate key and store in given container which name of container provide by the...
4 Feb 2012 by BillWoodruff
This notation will work:Int16[,] sbox1 = new Int16[,]{ {0x18,0x23,0xC6,0xE8,0x87,0xB8,0x01,0x4F,0x36,0xA6,0xD2,0xF5,0x79,0x6F,0x91,0x52}, {0x60,0xBC,0x9B,0x8E,0xA3,0x0C,0x7B,0x35,0x1D,0xE0,0xD7,0xC2,0x2E,0x4B,0xFE,0x57}, ...
10 May 2011 by BobJanova
Use DESCryptoServiceProvider.CreateDecryptor, and make sure you pass the same key and IV as you pass to the Javascript implementation. Then check that you've set the properties of the returned DES object for Mode and Padding to the same. The author claims that the JS implementation is compatible...
7 Sep 2012 by BrianHamilton
Managed to solve it myself.using System;using System.Text;using System.Windows.Forms;using System.Security.Cryptography;using System.Linq;using System.IO;using System.Runtime.Remoting.Metadata.W3cXsd2001;namespace MultipleHash{ public partial class Form1 : Form { ...
15 Sep 2012 by BrianHamilton
Is there any need to use IDisposable in the block of code below. I am availing of using and hash contains the SHA1 of text taken in from the user and inputData is a byte array. I assume the second block of code is correct.Example 1:using (SHA1 hash = SHA1.Create()){ txtSHA1.Text =...
8 May 2022 by Bruno Tabbia
Creation of a substitution box starting from a key and using it in a direct substitution cipher
30 Aug 2011 by cariolihome
Try to extend functionality of CryptDecodeObject function (http://msdn.microsoft.com/en-us/library/aa379871(v=vs.85).aspx[^]).For this You have to register custom OID decoding function in registry keyHKLM\Software\Microsoft\Cryptography\OID\EncodingType1\CryptDllDecodeObject\YourOID
19 Oct 2014 by CdnSecurityEngineer
Why would you want to do that? It seems awkward like you're trying to force your own will on Microsoft's tools etc. Here's why you really shouldn't do what you're asking. If you look at the Microsoft key container it looks like. ...
13 Feb 2016 by CDRxxx
HiI use this code to encrypt/decrypt files. It works fine. Now I want to change it for not having to write each decrypted file to disk, I want the decryption directly to a string variable...I try this adapted code but keep on getting empty strings...What is wrong???Thx for any help...
13 Feb 2016 by CDRxxx
This does the job:Function DecryptFileToString(Type As String, ByVal strInputFile As String, strOutputFile As String, ByVal PW As String) As String Dim Result As String = "" 'Setup streams to handle input and output. Dim fsInput As System.IO.FileStream ...
10 Feb 2014 by certoise
I have this code from Java Programming Oracle Press. Unfortunately, I can't find the error in this code. Could someone point out where is the problem?The exception I'm getting is javax.crypto.BadPaddingException (when run through Eclipse) andjavax.crypto.IllegalBlockSizeException (in...
19 Jun 2014 by chandra7531
Anyone know from where to download PGP Encryption assembly/DLL that can be referenced in C# code for further customization. I have found a similar kind of assembly provided by BouncyCastle but I am not sure whether to use it or not.Please do let me know from where i can get either an...
16 Feb 2022 by charles henington
Simple user defined Cipher Transform that I got the idea from https://www.codeproject.com/Articles/5319044/ARC4-Encryption-Library
10 Apr 2017 by CHill60
Loading 25000 items into a User Interface is just silly. That is the politest way I can put it. WPF collections? I think your friends are talking rubbish. How to speed up the load times? 1. You should implement some sort of paging - for example only load the first 40 items until the User...
31 Jul 2012 by Christian Amado
A very brief article about the implementation of encryption and decryption of a string in Silverlight Business Application
7 Aug 2012 by Christian Amado
You can Add your column in database (e.g. aspnet_users table), modify stored procedures that affects to your modified table. That's all from DB.Now in your aspnet project, Add a new class that extends from Membership or MembershipUser depends on your requirements. Add the property (column of...
4 Feb 2012 by Christian Graus
Wow. The reason you long how SOME errors, is that any number that has no letter in it, is a valid base 10 number. I believe you can use 0x, as 0xBD, to specify a number in hex. If you didn't specify it, how does the compiler tell between 55 and 0x55 ?
8 Oct 2010 by clairh
Can any1 please suggest me some links from where I could buy ocx or dll's that i could use to add in a mechanism in my vb6 project to encrypt binary files using SHA-1 or higher
5 Mar 2021 by Clark Fieseln
Low rate data exchange (e.g., chat) using audio steganography, ensuring privacy, anonymity and cybersecurity
12 May 2013 by compuknow
Is it possible to read a binary file such as .exe / .jpg files using C++ and encrypt it using some simple algorithm.The real question is how to read an entire .exe or jpg file into 1 dimensional array and manipulate it.
3 Jun 2013 by compuknow
I am trying to implement RSA using a C++ class. Below is the class :class rsacrypto{ long publickey; long privatekey; long modl; //Modulus public : rsacrypto(); //To be used to just generate private and public keys. rsacrypto(long &,long &,long...
5 Jun 2013 by compuknow
There are are many kinds of ciphers like caesar cipher,Vigenère Cipher,Bifid Cipher and many mor but how can these cipher techniques be applied to a binary file like a .exe file ?
7 Jun 2013 by compuknow
I had written a C++ program to perform the Schmidt - Samoa Public Key encryption. The code is as below :void keygen(long &publickey,long &privatekey,long &p,long &q){ p = genrndprimes(0,10); q = genrndprimes(10,30); long n = power(p,2)*q; long d =...
11 Jun 2013 by compuknow
I have the following expression for calculating the decryption key in a Public Key Encryption System :d = N-1 mod LCM(p-1,q-1)where N = p2q.I wrote the follwing code to find d ,long long int gendecrypkey(long long int modulo,long long int p,long long int q) { long...
13 Jun 2013 by compuknow
I wrote a code to generate a public key and a private key value. Below is the code :void keys(long long int &e_key,long long int &d_key,long long int phival) { e_key = genrndnum(100,(phival-1)); while(gcd(e_key,phival)!=1) { e_key =...
18 Jun 2013 by compuknow
I wrote the following C++ code for generating keys for RSA :void keygen(long long int &e_key,long long int &d_key,long long int phival) { //Code to find the encryption key. e_key = genrndnum(2,(phival)); while(gcd(e_key,phival)!=1) { ...
5 Dec 2012 by CPallini
Probaly (well, with very high probability) the SHA-256 doesn't satisfy all the requirements (from the Theoretical definition): "it is not sufficient to make a function "lossy" (not one-to-one) to have a one-way function".
18 Jun 2013 by CPallini
15 Jul 2013 by CPallini
Quote:How to encrypt image with AES algorithm?Possibly using a library.Quote:How much is the size difference (increase/decrease)after encryption? There would be no significative difference (data must be aligned to encription block, for instance 16 bytes, so you may experience a maximum...
14 Mar 2014 by CPallini
In this CodeProject article you may find: "Hash Functions: An Empirical Comparison"[^].
13 Oct 2015 by CPallini
As others already pointed out, the sentenceQuote:using Public key for communication so it is vulnerable is just wrong.Have a look at this Wikipedia page "Public-key cryptography"[^].
21 Dec 2016 by CPallini
Here some info: c++ - CreateProcess from memory buffer - Stack Overflow[^].
16 Jul 2017 by CPallini
14 Nov 2019 by CPallini
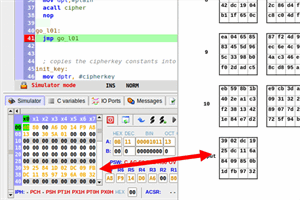
An assembly implementation of the AES-128 cipher algorithm for the 8051 microcontroller
19 Mar 2020 by CPallini
What about The Documentation[^]? Looks you are unfamiliar with the documentese (you should fix that as soon as possible). try const char mystr = "My Beautiful String"; // first parameter is the input string unsigned long len = strlen(...
20 Mar 2020 by CPallini
Quote: 31ed4989d15e4889e24883e4f050544c8d059a01 If that is the hexadecimal string representation of an array of bytes then you should do something like: unsigned char s[] = { 0x31, 0xed, 0x49, 0x89, ..., 0x01}; unsigned char h[20]; RIPEMD160(s,...