- home
- articles
- quick answersQ&A
-
discussionsforums
- CodeProject.AI Server
- All Message Boards...
- Application Lifecycle>
- Design and Architecture
- Artificial Intelligence
- ASP.NET
- JavaScript
- Internet of Things
- C / C++ / MFC>
- C#
- Free Tools
- Objective-C and Swift
- Database
- Hardware & Devices>
- Hosting and Servers
- Java
- Linux Programming
- Python
- .NET (Core and Framework)
- Android
- iOS
- Mobile
- WPF
- Visual Basic
- Web Development
- Site Bugs / Suggestions
- Spam and Abuse Watch
- featuresfeatures
- communitylounge
- help?
Everything / Security / Cryptography
Cryptography
cryptography
Great Reads
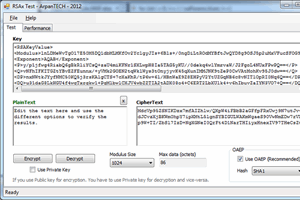
by Arpan Jati
RSA encryption library with full OAEP padding and private key encryption support
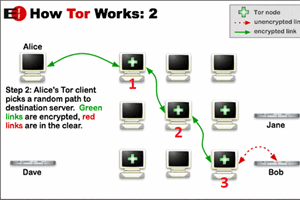
by Kewin Rausch
Design and development of a TOR-like protocol to keep your communication secure and your identity unknown
by Cryptonite
The Blum Micali algorithm provides for a cryptographically secure PRNG (pseudo random number generator).
Latest Articles
by Daniel Ramnath
C++,
by Daniel Ramnath
C++ OpenSSL 3.
by Michael Chourdakis
Use SHA-3 and the CRYSTALS Kyber,
by Sergey Alexandrovich Kryukov
Generator of highly secure passwords based on cryptographic hash and master password,
All Articles
15 Jul 2012 by
RSA encryption library with full OAEP padding and private key encryption support
15 Oct 2017 by Kewin Rausch
Design and development of a TOR-like protocol to keep your communication secure and your identity unknown
8 Feb 2022 by Pavel Bashkardin
7 May 2012 by Sergey Alexandrovich Kryukov
You should never ever store passwords in their original form. If you think about it: you never need them for authentication, as you can always compare encrypted log-in password with you stored encrypted password. With public-key cryptography, you also don't have to store a private key (which is...
23 Sep 2014 by Cryptonite
29 Jan 2018 by phil.o
5 Mar 2021 by Clark Fieseln
Low rate data exchange (e.g., chat) using audio steganography, ensuring privacy, anonymity and cybersecurity
14 Nov 2019 by CPallini
An assembly implementation of the AES-128 cipher algorithm for the 8051 microcontroller
19 Feb 2022 by Asif Bahrainwala
18 Apr 2011 by Nish Nishant
.NET comes with tons of Crypto APIs. Take a look here:http://msdn.microsoft.com/en-us/library/system.security.cryptography.aspx[^]You need to pick one based on whether you want one-way encryption, hashing, private keys, etc. Too many factors and choices there, so it's eventually up to...
28 Oct 2016 by Deepraj Thuraka
Tweaking of the Bouncy Castle library to make it work with SecP128r1 curve1251
7 Feb 2019 by Sibeesh Passion
Create own cryptocurrency and own private consortium network in Azure
31 Jul 2012 by Christian Amado
A very brief article about the implementation of encryption and decryption of a string in Silverlight Business Application
2 Sep 2014 by Cryptonite
This code gives a solution to the Chinese Remainder Theorem using totients instead of the Extended Euclidean algorithm.
21 Nov 2014 by Farzad E. (dNetGuru)
.Net framework provides two classes that implement AES, a native implementation that calls CAPI and AesManaged which is a purely managed implementation. Which one should you use ?
24 Mar 2016 by F-ES Sitecore
1 Feb 2011 by GoonerGator
Hi,I need to get a guid of 64 bits. I know that guid generation using COM will give me 128 bits. It might be a stupid question since I would like to think MS would want to keep it secret but no harm trying : Does anyone know how does it work ? Does it use MD5 ? I seem to have a hazy...
1 Feb 2011 by #realJSOP
I didn't read it, but this might answer your question:http://www.webdav.org/specs/draft-leach-uuids-guids-01.txt[^]
4 Jul 2011 by Alexander Galkin
Besides the cryptographic information about your actual key, the key files always contain some metadata, as to when the key was generated, whether it is packed, if so what kind of packing (base64 etc) was used to pack the key etc.Try to open your key in a notepad to see if you can get any...
25 Apr 2012 by Aescleal
If you're not familiar with classes and header files you're going to have fun implementing anything in C++. If I were you I'd wrap my head around includes and abstract data types and then use libcrypto which is part of the OpenSSL[^] distribution. It's a C library rather than a C++ one but it's...
14 Mar 2014 by CPallini
In this CodeProject article you may find: "Hash Functions: An Empirical Comparison"[^].
2 Feb 2016 by Dave Kreskowiak
Consider that both MD5 and SHA1 are both considered "broken" and should not be used for any security purpose what-so-ever. Using them to "secure" a password is considered bad practice and a security risk.Read up more on it, here[^].
27 Jan 2019 by Richard MacCutchan
Yes, you have got the AES key. It is just that many of the bytes are not printable alphanumeric characters. You need to understand that a byte can have any value between 0 and 255, and only some of those values equate to printable characters. Google will find you the full set. Given that this...
30 Oct 2019 by Richard Deeming
HMAC is a one-way cryptographic hash function. You cannot retrieve the plaintext from the hash. HMAC - Wikipedia[^]
8 May 2022 by Bruno Tabbia
Creation of a substitution box starting from a key and using it in a direct substitution cipher
30 Sep 2010 by vpnchoudhary
The sha1 hash generation tool can be used to generate hashes on a file. The has generated can be outputted in the form of dig/Hex/Base64. You may use this utility to verify the integrity of the file transported over internet to make sure they are safe from tampering.
16 Mar 2011 by Sergey Alexandrovich Kryukov
It's nearly impossible to compare security. Comparing security means breaking the cipher of real-life size of the key. Do you have any idea how much resources it may take? :-)Come to think about, the possibility of easy experimental comparison would present a back door (please see the...
18 Apr 2011 by #realJSOP
Like Nish said, there are way too many factors, situations, and possible requirements. We have no idea of the environment you're in, how secure it has to be, or anything even remotely associated with access control. It's a decision only you can make.
12 Sep 2011 by Ronald L
Hello Everyone,I have a question regarding the actual signature value on a X.509 v3 certificate. According to the recommendations stated in RFC 2459 and RFC 3280, the signature value should be located immediately after the signature algorithm. But all the certificates in my certificate...
2 Dec 2011 by OriginalGriff
If you are going to post your homework, at least try to make it look like you have attempted to do something yourself!We do not do your homework: it is set for a reason. It is there so that you think about what you have been told, and try to understand it. It is also there so that your tutor...
9 Oct 2012 by Sergey Alexandrovich Kryukov
[In reply to the OP's comment to Solution 1:]No, don't use SHA1 (or MD5) for any security purposes — they are found broken. Please read:http://en.wikipedia.org/wiki/Sha1[^],http://en.wikipedia.org/wiki/MD5[^].The most used reliable and secure cryptographic hash function would...
15 May 2013 by Richard C Bishop
Here is a site that might help:Clickety[^]You should really use a search engine next time you have such a basic question. It will save you and everyone else time. You will also get a wider range of answers.
3 Jun 2013 by Richard MacCutchan
15 Aug 2013 by OriginalGriff
MD5 is not an encryption algorithm - it is a hashing algorithm. The big difference is that encryption can be reversed, hashing can't. So once you have hashed your password (combined with the challenge key in some way) your password cannot be derived from the information you share with the...
25 Feb 2014 by Sergey Alexandrovich Kryukov
Please see my past answer, it shows most tricky part of it, manipulation with the header/metadata: Writting Header wav in wav.file[^].(You can automatically translate C# to VB.NET, but it's enough to understand the idea; I referenced the document I used.)See...
15 Nov 2014 by OriginalGriff
Simple: don't encrypt. If you don't encrypt, there is no key, so no way to work back.Instead, use Hashing - SHA is good - it converts the "licence info" you collect from the PC into a specific code which you then compare against the stored value. The key is long enough (and random looking...
15 Nov 2014 by Zoltán Zörgő
As you might have noticed, most of the manufacturers use the following architecture/flow for licensing:1) User gets a generic installer, without any licensee related information within. He/she installs the application.2) There is a code within and/or in a separate bundled application, that...
8 Dec 2015 by Afzaal Ahmad Zeeshan
Actually, you have not shown the implementation of this class. The following two snippets are just the "pseudo-code" for the algorithm. What do you think, did you implement it? Does the code work well? From the code, it is clear that i is zero, so only the first block would execute and a few...
24 Mar 2016 by OriginalGriff
This is one of the most common problems we get asked, and it's also the one we are least equipped to answer, but you are most equipped to answer yourself.Let me just explain what the error means: You have tried to use a variable, property, or a method return value but it contains null -...
1 Jun 2016 by Dave Kreskowiak
It's exploding probably because "SHA256" is not proper Oid descriptor.It should be: signer.DigestAlgorithm = new Oid("2.16.840.1.101.3.4.2.1");An "Internal server error" means that you haven't properly setup the objects and/or properties required to use the Signer. There's probably...
10 Apr 2017 by CHill60
Loading 25000 items into a User Interface is just silly. That is the politest way I can put it. WPF collections? I think your friends are talking rubbish. How to speed up the load times? 1. You should implement some sort of paging - for example only load the first 40 items until the User...
30 Oct 2019 by Dave Kreskowiak
HMAC is a cryptographic hash, not an encryption. You cannot get the original content back from the hash value.
22 Mar 2020 by k5054
looking back at your original question, you had const unsigned char* rawdata = "046EAF0968AA895ADDFEE599566F0B880242461D1377F4887C9B84631E13067B96DB18C41E0C208F8D12EBCC3F99F2522903AF6105833E4CBADE9D6A1D0F039187"; unsigned long n =...
14 Aug 2023 by Daniel Ramnath
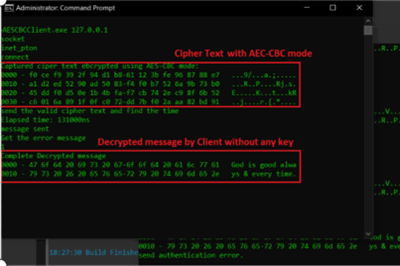
C++ OpenSSL 3.1 Attack AES-CBC using Padding Oracle Attack, and Timing Attack
8 Feb 2011 by Mario Majčica
Hi all,In order to access to the web service I need a certificate.I generated my certs:openssl genrsa 1024 > private.keyopenssl req -new -x509 -nodes -sha1 -days 1100 -key private.key > public.certhen merged this two into a pfx certificate byopenssl pkcs12 -in public.cer...
22 Feb 2011 by Dylan Morley
All the module should be designed by yourself.See this line here, Read it again. What is it telling you?
27 Feb 2011 by Manfred Rudolf Bihy
There is an article here on CP: A C++ Implementation of the Blowfish Encryption/Decryption method[^].Hope that helps you!
16 Apr 2011 by LaxmikantYadav
Hi Reena,Please find out the source code of Blowfish algorithm on below link.Down load from http://www.schneier.com
7 Mar 2011 by OriginalGriff
Yes, there will be, lots, but given that the shortest SHA is 160 bits, the odds on you finding one by randomly putting just 7 digits into the hashing algorithm are too small to list. How big is 2^160? That is kind of the idea of SHA: That you can't predict the value from the start data, and...
11 Mar 2011 by Albin Abel
First you have to decide which hash algorithm has to use. Because once you hashed the files then changing the algorithm will be a waste. There are lot of hash algorithms with .Net framework, Keyed and Non-Keyed. Each has different purpose. For example MD5 is good at small files. But for very...
18 Apr 2011 by OriginalGriff
To add to what SA said: When you store a hash of a password, do not hash the raw password either: include the UserID or UserName or other unique-to-this-user information with it before you generate the hash. Otherwise, if two users have the same password, they will have the same hash. This...
30 Apr 2011 by Sandeep Mewara
What else would you like to have sir? Some fries with a coke along with the code? :doh:It does not work like this here. I am sorry but there is no quick question here. This sounds like your college project/assignment, you should put some effort.We expect you to put some time in trying...
30 Apr 2011 by Richard MacCutchan
15 May 2011 by kastriotlimani
I have a project to implement use of s boxes of DES (data encryption standard) in win form application ..if anyone can help me with some ideas or hopefully to tell me some useful lines of code that would be helpful to me ... ps: I don't need all the des algorithm , just how s boxes work...
15 Jun 2011 by Sergey Alexandrovich Kryukov
How can you ask questions in such form: "anybody knows"? Many people here know this very well.First, if keys exist, they always send somewhere. Now, I feel you did not get it. How do you think, is it possible that two parties never meet, exchange data using some open channel and still can...
15 Jun 2011 by TorstenH.
simple approach:Decrypt in JAVA problem[^]..for "not so much security" systems. Depends on what you want to transmit on the network. this is a useful way when the stuff "just should not be readable by everybody". Implement that on both sides in case.
30 Jun 2011 by #realJSOP
24 Aug 2011 by Richard MacCutchan
You need to get yourself an introductory book or look at some of these tutorials[^].
29 Aug 2011 by barneyman
I'm in the process of creating a bunch of attribute certificates, using custom X509 extensions, that all works; this is just the backgroundWhen those certificates are displayed in the MMC Certificate Snapin, the OID's of my attributes aren't registered, so under the Certificate Details tab,...
30 Aug 2011 by cariolihome
Try to extend functionality of CryptDecodeObject function (http://msdn.microsoft.com/en-us/library/aa379871(v=vs.85).aspx[^]).For this You have to register custom OID decoding function in registry keyHKLM\Software\Microsoft\Cryptography\OID\EncodingType1\CryptDllDecodeObject\YourOID
17 Oct 2011 by
Randor
Hi,The CryptGenKey function[^] and the other Cryptography Functions[^] are exported from Advapi32.dll and you can use them on OS WINVER >= 5.0You should consider rephrasing your question... there are several different types of cryptography keys. If you are looking for a simple random...
23 Apr 2012 by Reza Ahmadi
Hi,Have you tried these posts:http://www.4guysfromrolla.com/articles/022107-1.aspx[^]http://msdn.microsoft.com/en-us/library/cc837966%28v=sql.100%29.aspx[^]the second one is applied to 2005 and 2008I hope it helps,Cheers
30 Jul 2012 by Dave Kreskowiak
There are pieces of information missing from your code snippet, namely, the implementation of "ValidateKeyAndIv" and what "_crypto" is and how it was created and setup.Your inner Try is not needed at all and I'd work on using more meaningful variable names. The days of one letter variables...
25 Aug 2012 by Joezer BH
Hey all, I need a good hash function (for strings) that will produce the same hash value for a specific string on different platforms, My app invovles a server farm, and a "bank" server, Each server produces hash "keys" for strings and the bank stores the keys.The Servers may later...
4 Oct 2012 by DaveAuld
There is no "Best", it is down to how you want to apply the crypto hash, data criticality, data range, computational cost etc. etc.Have a read of the various hash comparisons here; http://en.wikipedia.org/wiki/Comparison_of_cryptographic_hash_functions[^]Maybe edit your question with...
9 Oct 2012 by fjdiewornncalwe
30 Nov 2012 by Michal Kozel
Well this is questions that should not be asked as there is no answer to it.I recommend to use DES(Data encryption system) and AES(Advanced encryption system) as these encryption systems had chosen their underlying algorithms by standardization group and it's the best common option...
29 Dec 2012 by Espen Harlinn
On Windows you have the Crypto API[^] - which comes with a nice set of Cryptographic Service Providers[^]Best regardsEspen Harlinn
14 Jan 2013 by Monish cse
I am going to implement PKINIT in kerberos for my project. I am totally confused in starting the coding part, I know all the theoretical parts of kerberos like how client, KDC and Application server works. I want help in implementation part like,1. What are all the libraries and API's must...
20 Jan 2013 by Sergey Alexandrovich Kryukov
First of all, it's all already well implemented in .NET. Moreover, the digital signature itself is used in the very basic layers of .NET, first of all, due to the strongly-named assemblies (http://en.wikipedia.org/wiki/Strong_name[^]).So, there is nothing you will really have to implement....
17 Apr 2013 by jsolutions_uk
I still think you are thinking too much about the implementation rather than thinking about exactly what security you need, but maybe I'm wrong, so I'll try and provide some suggestions for the solution you are looking for :) :My understanding is that you cannot store symmetric keys in key...
26 Apr 2013 by StianSandberg
Rijndael/AES is a block cypher. It encrypts data in 128 bit (16 character) blocks. Cryptographic padding is used to make sure that last block of the message is always the correct size.You need to explicitly set the padding for both encryption and decryption.For example: mainRM.Padding =...
6 Oct 2013 by Garth J Lancaster
you're telling the API you're passing the input in as base-64 >> CRYPT_STRING_BASE64yet "MyTest" isnt a base-64 coded 'string'I wouldnt blame the api for chucking a mental, personally - its behaviour seems normal to me
12 Feb 2014 by Vedat Ozan Oner
error description says what the error is. Quote:"Specified key is not a valid size for this algorithm."let's check key which is "A0D1X0Q" which has the length of 7. you can find key sizes...
13 Feb 2014 by David Johns
In desperation, I contacted the author of RFC 5849 and he promptly replied this this address that shows my implementation was right all along:http://www.rfc-editor.org/errata_search.php?rfc=5849[^]Hopefully that helps someone else someday!
14 Mar 2014 by OriginalGriff
Loads!Lower security is nearly always faster, but you will have to do some timing tests yourself.Of you aren't interested in security, then there are loads of ways to hash stuff: MD5, CRC, even XOR and SUM.What you want too use will depend on your data, and how big your hash has to...
3 Jun 2014 by E.F. Nijboer
It wouldn't strengthen it. The reason for the random salt is to prevent creating a rainbow table. If you use a derived salt you would weaken the encryption. For example, it would render the result of GetSalt("Foo") to be "Bar". But it would always be "Bar"! There is nothing random about...
10 Jul 2014 by Yang Kok Wah
Padding is part of Block cipher implementation. Refer tohttp://msdn.microsoft.com/en-us/library/system.security.cryptography.paddingmode(v=vs.110).aspx[^]If you are using 8 block cipher,If you want to encrypt 9 bytes data FF FF FF FF FF FF Ff Ff FFUsing PaddingMode.ANSIX9237...
15 Nov 2014 by Debanshu Chatterjee
I have an application which will be used by various users, when user will start using the application it will generate one license file(encrypted) at the location where it is getting installed, and for each time application runs it will decrypt the file, will validate all parameters and update...
7 Jul 2015 by OriginalGriff
If you don't understand something complicated, then the place to start is Google: It led me very quickly to this tutorial series: AES (Rijndael) Explained[^] (You tube, four parts)As for the implementation and use, Google again is very helpfull: AES in C[^] provides a lot of resources, some...
3 Dec 2015 by George Jonsson
It depends if you have static library files (.lib) or only source code (.c)If you only have c-files, then you can add them to your project and include the header files where you need to. How to: Add Existing Items to a Project[^]If you have library files, see this link: MSDN: .Lib Files...
1 Dec 2015 by Albert Holguin
Here[^] are the build instructions for Windows (32bit, there's a different doc for 64bit). After you've built and installed the openssl libraries, add the include paths (openssl/include or inc32/) to your Visual Studio library paths and the library binary paths (openssl/lib or out32dll/) to your...
13 Feb 2016 by OriginalGriff
Don't put it to strings. Strings contain characters, not bytes, and there is a very good chance that the string representation of your data will be different to the original - which means that it won't decrypt!.Instead, use a byte array and it should work. The easiest way is to replace your...
26 Apr 2016 by OriginalGriff
As the error says, CreateEncryptor is not a string function - it's a method which is called on the selected encryption algorithm. For example: SymmetricAlgorithm.CreateEncryptor Method (System.Security.Cryptography)[^] orSymmetricAlgorithm.CreateEncryptor Method (Byte[], Byte[])...
21 Dec 2016 by CPallini
Here some info: c++ - CreateProcess from memory buffer - Stack Overflow[^].
7 Sep 2017 by Graeme_Grant
Google Search gods are your friend... This search: BouncyCastle documentation Pbkdf2 c#[^] found this accepted solution: How to create a PBKDF2-SHA256 password hash in C# / Bouncy Castle - Stack Overflow[^]
22 Nov 2017 by OriginalGriff
Technically, it's a hexadecimal number: there is little else that can be told from it. Numbers do not have an intrinsic "type" and there is no indication with a number of what algorithm (if any) was used to generate it, any more than you can discern from the number 120 that it was generated by...
13 Mar 2018 by F-ES Sitecore
You can't encrypt the file at the client. Well, you probably could but it's worthless as you'd need to expose your "secrets" allowing anyone to decrypt your data. If you want to avoid man in the middle attacks then use https, that's what it's there for.
12 Mar 2019 by OriginalGriff
Several things: 1) It may be urgent to you, but it isn't to us. All that your stressing the urgency does is to make us think you have left it too late, and want us to do it for you. This annoys some people, and can slow a response. 2) Never, ever, accept code from a insecure website to handle...
19 Mar 2020 by OriginalGriff
Have you considered reading the documentation: /docs/man1.0.2/man3/RIPEMD160.html[^] at all?
19 Mar 2020 by CPallini
What about The Documentation[^]? Looks you are unfamiliar with the documentese (you should fix that as soon as possible). try const char mystr = "My Beautiful String"; // first parameter is the input string unsigned long len = strlen(...
20 Mar 2020 by CPallini
Quote: 31ed4989d15e4889e24883e4f050544c8d059a01 If that is the hexadecimal string representation of an array of bytes then you should do something like: unsigned char s[] = { 0x31, 0xed, 0x49, 0x89, ..., 0x01}; unsigned char h[20]; RIPEMD160(s,...
20 Mar 2020 by Richard MacCutchan
const unsigned char* rawdata = ""; unsigned long n = strlen(rawdata); unsigned char md[32]; unsigned char* pmd = RIPEMD160(rawdata, n, md);
20 Mar 2020 by phil.o
const unsigned char* rawdata = "046EAF0968AA895ADDFEE599566F0B880242461D1377F4887C9B84631E13067B96DB18C41E0C208F8D12EBCC3F99F2522903AF6105833E4CBADE9D6A1D0F039187"; You've already been told that, but I am going to tell you once more: the rawdata...
22 Mar 2020 by steveb
when you are using an initialization list (your 2nd case) you need to change your declaration to: const unsigned char rawdata[] = { 0x04, 0x6E, 0xAF, 0x09, 0x68, 0xAA, 0x89, 0x5A, 0xDD, 0xFE, 0xE5, 0x99, 0x56, 0x6F, 0x0B, 0x88, 0x02, 0x42, 0x46,...
27 Mar 2020 by Richard MacCutchan
OK, this is what it is: Base58Check encoding - Bitcoin Wiki[^]
13 May 2020 by Apprieu (Apprieu)
23 Sep 2020 by Richard Deeming
This would require the attacker to have a valid certificate for the domain they're trying to intercept. There are generally two ways this can happen: A rogue or compromised CA. This tends to be caught fairly quickly, and that CA will be booted...
4 Mar 2021 by Dave Kreskowiak
This took all of 20 seconds to find: Quote: Provides cryptographic algorithm implementations and key management for non-Windows systems with OpenSSL. NuGet Gallery | System.Security.Cryptography.OpenSsl 5.0.0[^] And on RSAOpenSsl Class...
25 Oct 2021 by ADMGNS