Hack proof your ASP.NET applications from Sensitive Data Exposure and Information Leakage
4.81/5 (19 votes)
This Article describe How Developer unintentionally Expose the Sensitive Data / Information leakage and How to prevent it.
Introduction
This is Part 4 of my series Hack proof your asp.net application.In this article ,I will describe How we sometimes unintentionally expose some sensitive information or leak some information to a hacker , who used that information to hack us. Keeping These terms separate "Sensitive Data exposure" which can directly harm to an individual or an organization, "Information leakage" are which helps attacker to perform malicious activities.Both terms are correlated and we can say Information leakage can contain Sensitive data exposure and vice versa.
Background
You can read previous article of this series from below links :
Sensitive Data Exposure:
First thing you need to find out what is "Sensitive Data" for your business.What are your business "terms and conditions" or what are your "policies" or what offerings you are providing to your consumer or customer. Sensitive Data are which can directly harm an individual or an organization.
Sensitive Data includes password , credit card , personal information and may include email depends on the business policy of different website.
Impact of Sensitive Data Exposure :
Sensitive Data may exposed accidentally(application error or application bug) and maliciously done by any hacker.
- Negative Impact on consumer and business integrity,
- Financial loss(from business loss/credit card exposed details misuse),
- Can expose credit card detail , passwords etc.
Multiple points where sensitive data may exposed by an ASP.NET application :
 As we can see in above image there is no palace which is safe , an attacker can try to get sensitive data from victim(client) machine , victim browser (cache) , server's config , log and temp file ,database (using SQL injection or from config file).
As we can see in above image there is no palace which is safe , an attacker can try to get sensitive data from victim(client) machine , victim browser (cache) , server's config , log and temp file ,database (using SQL injection or from config file).
How to prevent from Sensitive Data Exposure:
Sensitive Data can be exposed Internally and externally.
- To prevent insider attack you need to control who gain access to your application and data backup,
- To prevent Outsider attack you need to encrypt all the "Sensitive Data" on the network,
- Secure storing of password in .NET applications (Secure passwords in asp.net),
- Disable Caching for pages that contains sensitive data,
In HTML page :
Add following META tags in Header of the page-
<META HTTP-EQUIV="PRAGMA" CONTENT="NO-CACHE"> <META HTTP-EQUIV="CACHE-CONTROL" CONTENT="NO-CACHE">
In ASP.NET applications:
Response.Cache.SetCacheability(System.Web.HttpCacheability.NoCache);
Response.Cache.SetNoStore();
Or set the ouput directive in .aspx page, that cache should expire in 0 seconds.
<%@ OutputCache Duration="0" VaryByParam="None" %>
In ASP.NET MVC applications:
Disable for all actions in a controller -
OutputCacheAttribute(VaryByParam = "*", Duration = 0, NoStore = true)] // will be applied to all actions in MyController, unless those actions override with t heir own decoration
public class MyController : Controller
{
// ...
}
Disable for particular action-
public class MyController : Controller
{
[OutputCacheAttribute(VaryByParam = "*", Duration = 0, NoStore = true)] // w ill disable caching for Index action only
public ActionResult Index()
{
return View();
}
}
5. Turn off Auto-complete on the page where you are collecting sensitive data.
<form id="Form1" method="post" runat="server" autocomplete="off"> //for whole page Or for a specific TextBox : <input type= "text" autocomplete="off"/> // in simple html <asp:TextBox ID="Textbox1" Runat="server" autocomplete="off"></asp:TextBox> //in asp.net aspx page
6. Do not store sensitive data unnecessary (Like Many Online payment gateway do , they do not store credit card details they just pass it and forget it) , if you want to store such details then they must me PCI/DSS compliance .Including some
- Protect stored cardholder data
- Encrypt transmission of cardholder data across open, public networks.
Encrypt of config file is it really necessary in asp.net? Nowadays i thought no because IIS7 does not allow to directly access config file from url. IIS7 restricted it by default , they filter every request from <requestfiltering> , learn more about it (Request Filtering) .However if a web server has been compromised allowing remote access to the server itself, then having an encrypted web.config file will be the least of your worries :P :D.
Information leakage :
Revealing System data or debugging information helps an attacker to learn about the system and form a plan of attack accordingly.Information leakage is not direct attack, its just help an attacker to gather information about system which helps him to do any another attack.
What Can an attacker gathers ?
- Software versions(so attacker can try to find the vulnerabilities of that particular version)
- System Types(SQL server, IIS, MySQL etc.. )
- Login ID and Email address (Now attacker just have to find your password)
- Tracing and debugging information
How an attacker gathers Information ?
An attacker behaves likes an detective who collects all the information about the victim.There are some of ways how they do it :
1. Search Engines : Search engine index information about every website and attacker do take benefit from that.
- Index debug/trace information
- Find any organization documents
- Index private content
- Index errors

2. Fiddling with application(forcing errors,analyzing HTTP headers etc..)
3. Automated scanning tools.
 Tracing information may expose :
Tracing information may expose :- connection string (credentials)
- Your application framework version (Helps attacker to form attack according to framework vulnerability)
- Virtual directory path
2. Find organization documents
site:www.[domain_name].com .xls .doc .ppt //Precede your query with site: if you know you want your answer from a specific site or type of site
Attacker try to cause error in any application(Asp.net) ,and gathers information about their version. In worst cases they do gather connection-string , credentials etc..

- Connection string is exposed by causing an error into any asp.net application (This is the worst case, i am just showing what attacker do hack any asp.net application,and i know nobody use this coding standard nowadays,but still.)
- Coding implementation style
- Physical location of an application
- Asp.net version is exposed
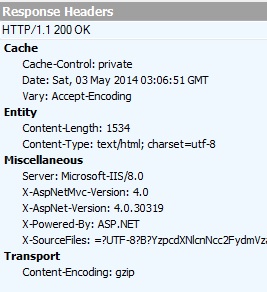
- MVC application
- Framework version is 4.0
- Server is Microsoft-IIS
5. Login page/Sign up page helps attacker to know the Email Address is valid or not (example: Hackers try on many web application to login with administrator@domain.com , they can confirm this email by sign up page when sign up page will tell id already exist)
All above mentioned are just some example how an attacker gathers information about an application.There might be some other ways too.
How to Prevent Asp.net Application from Information Leakage :
1. Always redirect to an Error page when any error occurs (Don't reveal anything from error)
In Asp.Net application :
Step 1: Create an error page/pages accordingly to the error
Step 2: In Application web.config set the default redirection when any error occurs :
<system.web> <customErrors mode="RemoteOnly" defaultRedirect="~/Error.aspx"></customErrors> <!-- your rest configuration of system.web--> </system.web>
Custom error node will cause an application to redirect to defaultRedirect node value page. There are three mode in customErrors On/Off/RemoteOnly . I personally use RemoteOnly because its automatically works only when application deployed not at the time of development so i can see the errors at the time of development and can fix them.
Using customErrors node you can redirect according to the status code of Response Headers:
<customErrors mode="RemoteOnly" defaultRedirect="~/ErrorPages/Oops.aspx">
<error statusCode="404" redirect="~/ErrorPages/404.aspx" />
</customErrors>
In Asp.Net MVC application :
Step1 : Create an Error Controller
Step2 : Again like asp.net application set it to web.config
<customErrors mode="On" defaultRedirect="~/Error"> <error redirect="~/Error/NotFound" statusCode="404" /> </customErrors>
For different status code you can redirect to different views from controller:
public class ErrorController : Controller
{
public ViewResult Index()
{
return View("Error");
}
public ViewResult NotFound()
{
Response.StatusCode = 404;
return View("NotFound");
}
}
Default Error view : (you can create according to the status code as well)
@model System.Web.Mvc.HandleErrorInfo @{
ViewBag.Title = "Error";
} <hgroup class="title">
<h1 class="error">Error.</h1>
<h2 class="error">An error occurred while processing your request.</h2>
</hgroup>
2. Disable tracing
Set trace enabled = false in web.config for both Asp.Net and Asp.Net MVC application in <system.web> node.
<trace enabled="false"/>
3.Always Deploy in Release Mode

Tip : Above mentioned Point 1,2,3 can be achieve using Asp.net feature of RetailMode .
RetailMode is little known feature of Asp.Net which Turn on Custom Error , Disable tracing , Compiles in release mode for all the application running on a System.
- Turns on Custom Error
- Disable Tracing
- Compile in Release Mode
How to Turn Retail Mode on ?
C:\Windows\Microsoft.NET\Framework\v4.0.30319\Config C:\Windows\Microsoft.NET\Framework\"Your Version of framework"\Config
Step 2: Open machine.config file > find <system.web> node
Step 3: under this Enable retail mode :
<deployment retail="true" />

4. Remove Unnecessary HTTP headers
The X-AspNet-Version, X-AspNetMvc-Version, X-Powered-By, and Server
- Removing
X-AspNet-Version: Under<System.web>add this<httpRuntime enableVersionHeader="false"/> - Removing
X-AspNetMvc-Version: Add this inGlobal.asax.cxfileMvcHandler.DisableMvcResponseHeader = true; - Remove Server Header : Refer this link
- Remove or Edit
X-Powered-By: IIS7 Manager > HTTP Response Header > Remove


