
Searching Google for downloads of popular software has always come with risks, but over the past few months, it has been downright dangerous, according to researchers and a pseudorandom collection of queries.
“Threat researchers are used to seeing a moderate flow of malvertising via Google Ads,” volunteers at Spamhaus wrote on Thursday. “However, over the past few days, researchers have witnessed a massive spike affecting numerous famous brands, with multiple malware being utilized. This is not ‘the norm.’”
One of many new threats: MalVirt
The surge is coming from numerous malware families, including AuroraStealer, IcedID, Meta Stealer, RedLine Stealer, Vidar, Formbook, and XLoader. In the past, these families typically relied on phishing and malicious spam that attached Microsoft Word documents with booby-trapped macros. Over the past month, Google Ads has become the go-to place for criminals to spread their malicious wares that are disguised as legitimate downloads by impersonating brands such as Adobe Reader, Gimp, Microsoft Teams, OBS, Slack, Tor, and Thunderbird.
On the same day that Spamhaus published its report, researchers from security firm Sentinel One documented an advanced Google malvertising campaign pushing multiple malicious loaders implemented in .NET. Sentinel One has dubbed these loaders MalVirt. At the moment, the MalVirt loaders are being used to distribute malware most commonly known as XLoader, available for both Windows and macOS. XLoader is a successor to malware also known as Formbook. Threat actors use XLoader to steal contacts' data and other sensitive information from infected devices.
The MalVirt loaders use obfuscated virtualization to evade end-point protection and analysis. To disguise real C2 traffic and evade network detections, MalVirt beacons to decoy command and control servers hosted at providers including Azure, Tucows, Choopa, and Namecheap. Sentinel One researcher Tom Hegel wrote:
As a response to Microsoft blocking Office macros by default in documents from the Internet, threat actors have turned to alternative malware distribution methods—most recently, malvertising. The MalVirt loaders we observed demonstrate just how much effort threat actors are investing in evading detection and thwarting analysis.
Malware of the Formbook family is a highly capable infostealer that is deployed through the application of a significant amount of anti-analysis and anti-detection techniques by the MalVirt loaders. Traditionally distributed as an attachment to phishing emails, we assess that threat actors distributing this malware are likely joining the malvertising trend.
Given the massive size of the audience threat actors can reach through malvertising, we expect malware to continue being distributed using this method.
Google representatives declined an interview. Instead, they provided the following statement:
Bad actors often employ sophisticated measures to conceal their identities and evade our policies and enforcement. To combat this over the past few years, we’ve launched new certification policies, ramped up advertiser verification, and increased our capacity to detect and prevent coordinated scams. We are aware of the recent uptick in fraudulent ad activity. Addressing it is a critical priority and we are working to resolve these incidents as quickly as possible.
Anecdotal evidence that Google malvertising is out of control isn’t hard to come by. Searches seeking software downloads are probably the most likely to turn up malvertising. Take, for instance, the results Google returned for a search Thursday looking for “visual studio download”:
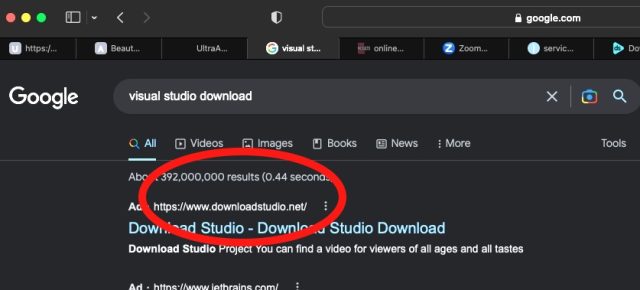
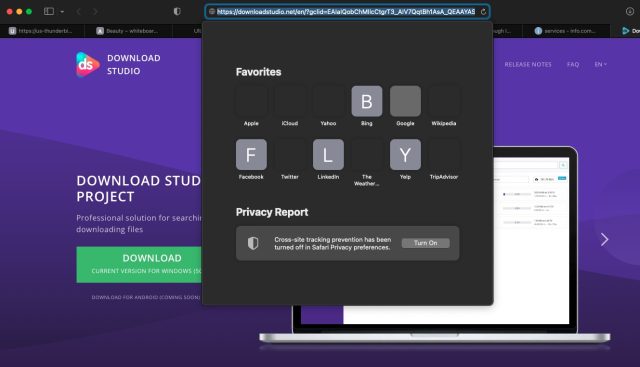
Clicking that Google-sponsored link redirected me to downloadstudio[.]net, which is flagged by VirusTotal as malicious by only a single endpoint provider:
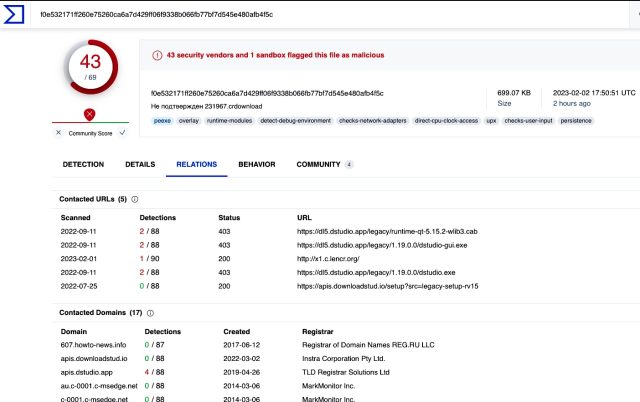
On Thursday evening, the download this site offered was detected as malicious by 43 antimalware engines:
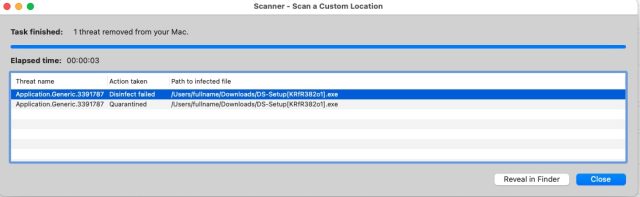
The download is malicious:
reader comments
167