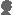
Introduction
Any software can be analyzed step-by-step from a debugger! A debugger is a valid instrument in order to discover bugs, but most times it is used by the hackers/crackers in order to alter the routines of protection of our programs, or worse, in order to reverse engineer an entire algorithm!
Background
It is present, in Windows systems, an API function called IsDebuggerPresent (contained in kernel32.dll). It serves to verify the presence of a debugger. This function does not exist in Windows 95. It is also interesting to see using Pointers from VB.NET!
Example code (VB.NET):
Declare Function IsDebuggerPresent Lib "kernel32" () As Integer
Dim chkDebug as Integer = IsDebuggerPresent
chkDebug = 0 --> not debugged
chkDebug = 1 --> debugged
Using the code
It is supposed, in this demonstration, to use the SoftIce debugger.
It seems all simple, I can stop a hacker! Unfortunately, the truth is very different as our adversary can behave itself:
- Starts the debugger;
- It presses ctrl+d;
- It writes
BPX IsDebuggerPresent;
- Presses F5 in order to send in execution of the program, and magically a window similar to this appears (code assembler x86):
001B:77E52740 64A118000000 MOV EAX, FS:[00000018]
001B:77E52746 8B4030 MOV EAX, [EAX+30]
001B:77E52749 0FB64002 MOVZX EAX, BYTE PTR [EAX+02]
001B:77E5274D C3 RET
Therefore, it does not have to make other changes than to modify the value of return of the function and/or to make the patch directly for the library kernel32.dll:
001B:77E52749 0FB64002 MOVZX EAX, BYTE PTR [EAX+02]
It becomes:
001B:77E52749 33C0 XOR EAX, EAX
001B:77E5274B 90 NOP
001B:77E5274C 90 NOP
Our adversary is a good reverser! But from that what can we make? We can make a check on the BPX presence. BPX means to virtually put the value hex 0CCh in a determined memory area. In order to resolve this problem, we gain the address of the memory that interests us (in this case, on my WinXP home) 77E52740h, and verifies if it exists, in one of the 14 bytes, an equal value to 0CCh! It seems all very simple.
We use the APIs:
Declare Function LoadLibrary Lib "kernel32" Alias _
"LoadLibraryA" (ByVal lpLibFileName As String) As Integer
Declare Function FreeLibrary Lib "kernel32" Alias _
"FreeLibrary" (ByVal hLibModule As Integer) As Integer
Declare Function GetProcAddress Lib "kernel32" Alias _
"GetProcAddress" (ByVal hModule As Integer, _
ByVal lpProcName As String) As Integer
And we proceed as follows:
- We load in memory the library kernel32.dll;
- We find with
GetProcAddress the address of the API IsDebuggerPresent;
- We analyze the memory area.
Example code (VB.NET):
Dim hLib As Integer = LoadLibrary("kernel32")
Dim apiaddress as integer = GetProcAddress(hLib, _
"IsDebuggerPresent")
Dim memdebug(13) As Byte
Marshal.Copy(IntPtr.op_Explicit(apiaddress), _
memdebug, _
0, _
memdebug.Length)
Dim bFlag as Boolean = False
Dim ij As Integer
For ij = 0 To memdebug.Length - 1
If memdebug(ij) = &HCC Then
bFlag = True
Exit For
End If
Next ij
FreeLibrary(hLib)
If bFlag Then
End If
Clearly, this is only an example! You can analyze and check any portion of memory to leave from its address.
Points of Interest
Stopping the Reverse engineering of our programs puts in difficulty hackers/crackers...at least those who are not too much good!
Other articles from the author:
For other information, please visit my web site (in continuous modernization).
History
September 2004: First public release. (Sorry for my bad English...I'm Italian.)
President of "Cantelmo Software" (micro-ISV situated in Lizzanello (Lecce) - Italy): Development Software and Professional Component for .NET Platform. Author of Goliath .NET Obfuscator
 General
General  News
News  Suggestion
Suggestion  Question
Question  Bug
Bug  Answer
Answer  Joke
Joke  Praise
Praise  Rant
Rant  Admin
Admin 







 this .NET demo application protected with my simple obfuscator
this .NET demo application protected with my simple obfuscator 



 and vote?
and vote?