Table of Contents
- Introduction
- List of Services
- services.exe
- Signatures
- Structure of SERVICE_RECORD
- Life After Windows Vista
- Patching
- Search of Signatures
- Service Hiding
- Correct Restoration
- Structure of the Project Files
- References
- History
In this article, we continue investigation in the field of hiding application in the system. This theme was started by Ivan Romanenko and Sergey Popenko in the article “Driver to Hide Processes and Files”. Our aim is to discover the ways of application hiding in the system for the wide audience. The approaches described can be used in the Corporate Security systems development – to hide system agents and prevent switching them off by users. Information can also be useful for those who research harmful software - to build the adequate answer for the threats.
This article will tell where Windows OS stores the services and how it uses them. We’ll discuss how this knowledge can be applied to finding our custom service and hiding it.
So let’s start our research.
At the first step of my research, I thought that if there were services then somewhere their manager had to be. And it proved to be true – such a manager is in the file named services.exe.
The process services.exe deals with all operations associated with services, service manager – which is familiar to many developers by the ::OpenSCManager function, and obviously with the service storing too.
So my first task is to find where the service database is stored.
My analysis showed that we need ScInitDatabase function and it includes such assembler instructions:
ScInitDatabase proc near
xor eax, eax
push esi
mov g_uScTotalNumServiceRecs, eax
mov g_ImageDatabase, eax
mov g_pImageDatabase, eax
mov g_ServiceDatabase, eax
mov g_pServiceDatabase, eax
call ?ScInitGroupDatabase@@YGXXZ
mov esi, ds:__imp__RtlInitializeResource@4
push offset ?ScServiceRecordLock@@3VCServiceRecordLock@@A
CServiceRecordLock ScServiceRecordLock
mov ?ResumeNumber@@3KA, 1
call esi
push offset ?ScServiceListLock@@3VCServiceListLock@@A
CServiceListLock ScServiceListLock
call esi
push offset ?ScGroupListLock@@3VCGroupListLock@@A
call esi
call ?ScGenerateServiceDB@@YGHXZ
neg eax
sbb eax, eax
neg eax
pop esi
retn
ScInitDatabase end
I marked out some lines with red, they are suspected to store the data we need – service database g_pServiceDatabase. On the basis of the places where ScCreateServiceRecord and ScGetNamedServiceRecord variables are used, we can say that it is exactly what we are looking for – service database and the pointer to its beginning.
Without a second thought, we take this method as a basis as it is called only once at the program start, and choose signature to search pointer to the beginning of the list of services in the process memory.
Let’s consider the first variant A3 9C A0 01 01 A3 98 A0 01 01 E8 B5 08 00 00, which is just the assembler code of the three mentioned lines:
mov g_ServiceDatabase, eax
mov g_pServiceDatabase, eax
call ?ScInitGroupDatabase@@YGXXZ
To use this signature, we should guarantee that:
- All versions of services.exe have the same signature in the proper place
- All versions of services.exe have only one such signature
I developed the simple utility based on the code of FindSignature function (plServicesSiganture.cpp):
unsigned char g_ServicesDBSignature[] =
{ 0xA3, 0x9C, 0xA0, 0x01, 0x01, 0xA3, 0x98, 0xA0,
0x01, 0x01, 0xE8, 0xB5, 0x08, 0x00, 0x00 };
unsigned char g_ServicesDBSignatureMask[] =
{ 0xFF, 0xFF, 0xFF, 0xFF, 0xFF, 0xFF, 0xFF, 0xFF,
0xFF, 0xFF, 0xFF, 0xFF, 0xFF, 0xFF, 0xFF };
int
FindSignature ( char* pBaseAddr, unsigned long ulSectionSize,
unsigned long *pulSignatureOffset )
{
char* pFoundPos = 0;
char* pCheckPos = 0;
MASK_BUFFER bufMask = { (char*)g_ServicesDBSignature,
(char*)g_ServicesDBSignatureMask,
sizeof ( g_ServicesDBSignature ) / sizeof ( g_ServicesDBSignature[0] ) };
BUFFER bufMemory = { pBaseAddr, ulSectionSize };
if ( PL_STATUS_SUCCESS != PlSearchSequence ( &bufMask,
&bufMemory,
&pFoundPos ) )
{
return 0;
}
bufMemory.pStart = pFoundPos + 1;
bufMemory.nSize = ulSectionSize - (pFoundPos - pBaseAddr + 1);
if ( PL_STATUS_SUCCESS == PlSearchSequence ( &bufMask,
&bufMemory,
&pCheckPos ) )
{
return 0;
}
*pulSignatureOffset = (unsigned long)(pFoundPos - pBaseAddr);
return 1;
}
I started with services.exe for Windows XP and then checked all mentioned requirements for the signature for the rest of the services.exe versions for other OS versions. That gave me the final variant of the signature, which suited all versions and requirements:
68 XX XX XX XX C7 XX XX XX XX XX 01 00 00 00
where XX is any value that means that we should search the signature by mask.
This signature is pointing to the execution of the following commands from ScInitDatabase function:
push offset ?ScServiceRecordLock@@3VCServiceRecordLock@@A
CServiceRecordLock ScServiceRecordLock
mov ?ResumeNumber@@3KA, 1
Service database is the list of structures SERVICE_RECORD, which contain necessary description of each service for the system. Here we won’t discuss the complete structure SERVICE_RECORD as far as it’s not necessary for us.
My further research discovered three fields:
Prev – pointer to the previous list elementNext – pointer to the next list elementServiceName – pointer to the string with the service name
The offsets of these fields relative to the SERVICE_RECORD structure beginning are:
Prev – 0x00Next – 0x04ServiceName – 0x08
Windows Vista release “changed the world” – and it affected services.exe also.
The search for the list beginning changed and so did the structure of SERVICE_RECORD. Now dereferencing should be applied to the pointer to the service list beginning (it must be the common improved protection of the pointers in the process memory) and also I had to look for the new offsets of Next, Prev and ServiceName fields.
Here are these offsets:
Prev – 0x00Next – 0x60ServiceName – 0x04
Changes in the logic of the database beginning search are reflected in the functions SearchForServicesDbOffset_EarlierVista and SearchForServicesDbOffset_Vista (in the file plServicesSignature.cpp).
Below we’ll discuss the difficulties of the practical implementation.
To search for the signatures, we should look through the memory of the “services.exe” process and detect a signature. So we examine all memory allocated by this process using VirtualQueryEx and ReadProcessMemory functions:
MEMORY_BASIC_INFORMATION mbi;
if ( ::VirtualQueryEx ( hProcess, 0, &mbi, sizeof(mbi) ) != sizeof(mbi) )
throw std::exception ( "Error on VirtualQueryEx" );
void* pAddr = mbi.AllocationBase;
do
{
MEMORY_BASIC_INFORMATION mbi1;
if ( ::VirtualQueryEx ( hProcess, pAddr, &mbi1, sizeof(mbi1) ) != sizeof(mbi1) )
throw std::exception ( "Error on VirtualQueryEx" );
if ( mbi1.RegionSize != 0 )
{
std::vector< unsigned char > bufMemory ( mbi1.RegionSize );
SIZE_T nBytesRead = 0;
if ( ::ReadProcessMemory ( hProcess, pAddr, &bufMemory[0],
mbi1.RegionSize, &nBytesRead ) )
{
}
}
else
{
throw std::exception ( "No more process memory" );
}
pAddr = (PBYTE)pAddr + mbi1.RegionSize;
} while ( true );
After that, we find the beginning of the service list by the signature.
Now we should only find our record in the list and redefine the Next pointer of the previous record to the record which is next to our one, and correspondingly the Prev pointer of the next to our record should be redefined to the record which is previous to our one:
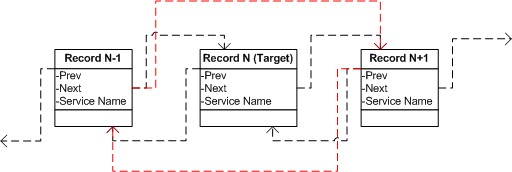
PUCHAR pServiceRecord = 0;
if ( !LookupServicesDbRecordByName
( hProcess, pServiceDb, pServicesContext, pwstrServiceName, &pServiceRecord ) )
{
false;
}
std::vector< unsigned char > buffer
( pServicesContext->m_OffsetFncList.m_fncGetEstimatedSize () );
if ( !::ReadProcessMemory ( hProcess, pServiceRecord, &buffer[0],
pServicesContext->m_OffsetFncList.m_fncGetEstimatedSize (), 0 ) )
{
throw std::exception ( "Error on ReadProcessMemory" );
}
PUCHAR pPrevServiceRecord = (unsigned char*)*(PULONG)pServicesContext->
m_OffsetFncList.m_fncGetOffset_Prev ( &buffer[0] );
PUCHAR pNextServiceRecord = (unsigned char*)*(PULONG)pServicesContext->
m_OffsetFncList.m_fncGetOffset_Next ( &buffer[0] );
if ( pPrevServiceRecord )
{
ulPatchAddr = (ULONG)pNextServiceRecord;
PUCHAR pPrevNextServiceRecord = (PUCHAR)pServicesContext->
m_OffsetFncList.m_fncGetOffset_Next ( pPrevServiceRecord );
SIZE_T szWritten = 0;
if ( !::WriteProcessMemory ( hProcess,
pPrevNextServiceRecord,
&ulPatchAddr,
sizeof (ulPatchAddr),
&szWritten ) )
{
throw std::exception ( "Error on WriteProcessMemory" );
}
}
if ( pNextServiceRecord )
{
ulPatchAddr = (ULONG)pPrevServiceRecord;
PUCHAR pNextPrevServiceRecord = (PUCHAR)pServicesContext->
m_OffsetFncList.m_fncGetOffset_Prev ( pNextServiceRecord );
if ( !::WriteProcessMemory ( hProcess,
pNextPrevServiceRecord,
&ulPatchAddr,
sizeof (ulPatchAddr),
0 ) )
{
throw std::exception ( "Error on WriteProcessMemory" );
}
}
After these manipulations, our service disappears.
Hiding is good but I should tell about restoration too to complete the story.
Why restore? To delete service correctly by means of corresponding DeleteService function.
My proposition is to create a callback function that returns the address of the hidden service in the memory of the “services.exe” process after the hiding. Then we will be able to easily restore the services sequence when we need it.
We should remember that the system is permanently changing and Prev and Next pointers of the hidden record cannot be the “live” records in the service list already.
That’s why while restoring, we should make such steps:
- Search the record which corresponds to the
Prev address; if there is such a record, then add element to the list after the specified element (InsertAfter). - If the record is not found, then search the record by the corresponding
Next address. If it is found, then add element to the list before the specified element (InsertBefore). - If the record is not found by Next pointer, then simply add the service to the end of the service list (
InsertAtTheEnd).
std::vector< unsigned char > buffer
( pServicesContext->m_OffsetFncList.m_fncGetEstimatedSize () );
if ( !::ReadProcessMemory ( hProcess, pServiceRecord, &buffer[0],
pServicesContext->m_OffsetFncList.m_fncGetEstimatedSize (), 0 ) )
{
throw std::exception ( "Error on ReadProcessMemory" );
}
PUCHAR pPrevServiceRecord = (unsigned char*)*(PULONG)pServicesContext->
m_OffsetFncList.m_fncGetOffset_Prev ( &buffer[0] );
if ( pPrevServiceRecord )
{
bool bFound = LookupServicesDbRecordByAddr ( hProcess, pServiceDb,
pServicesContext, pPrevServiceRecord, &pPrevServiceRecord );
if ( bFound )
{
InsertAfterPreviousRecord ( hProcess, pServicesContext,
pServiceRecord, pPrevServiceRecord );
return true;
}
}
PUCHAR pNextServiceRecord = (unsigned char*)*(PULONG)pServicesContext->
m_OffsetFncList.m_fncGetOffset_Next ( &buffer[0] );
if ( pNextServiceRecord )
{
bool bFound = LookupServicesDbRecordByAddr ( hProcess, pServiceDb,
pServicesContext, pNextServiceRecord, &pNextServiceRecord );
if ( bFound )
{
InsertBeforeNextRecord ( hProcess, pServicesContext,
pServiceRecord, pNextServiceRecord );
return true;
}
}
bool bFound = LookupServicesDbRecordByEnd ( hProcess, pServiceDb,
pServicesContext, &pPrevServiceRecord );
if ( !bFound )
{
return false;
}
InsertAsLastRecord ( hProcess, pServicesContext, pServiceRecord, pPrevServiceRecord );
return true;
The source code of the usermode application which illustrates everything told here is in the archive attached.
Jeffrey Richter, Christophe Nasarre. Windows via C/C++. Especially the chapter devoted to the Virtual memory research.
- 8th December, 2009: Initial post
ApriorIT is a software research and development company specializing in cybersecurity and data management technology engineering. We work for a broad range of clients from Fortune 500 technology leaders to small innovative startups building unique solutions.
As Apriorit offers integrated research&development services for the software projects in such areas as endpoint security, network security, data security, embedded Systems, and virtualization, we have strong kernel and driver development skills, huge system programming expertise, and are reals fans of research projects.
Our specialty is reverse engineering, we apply it for security testing and security-related projects.
A separate department of Apriorit works on large-scale business SaaS solutions, handling tasks from business analysis, data architecture design, and web development to performance optimization and DevOps.
Official site: https://www.apriorit.com
Clutch profile: https://clutch.co/profile/apriorit
 General
General  News
News  Suggestion
Suggestion  Question
Question  Bug
Bug  Answer
Answer  Joke
Joke  Praise
Praise  Rant
Rant  Admin
Admin 







